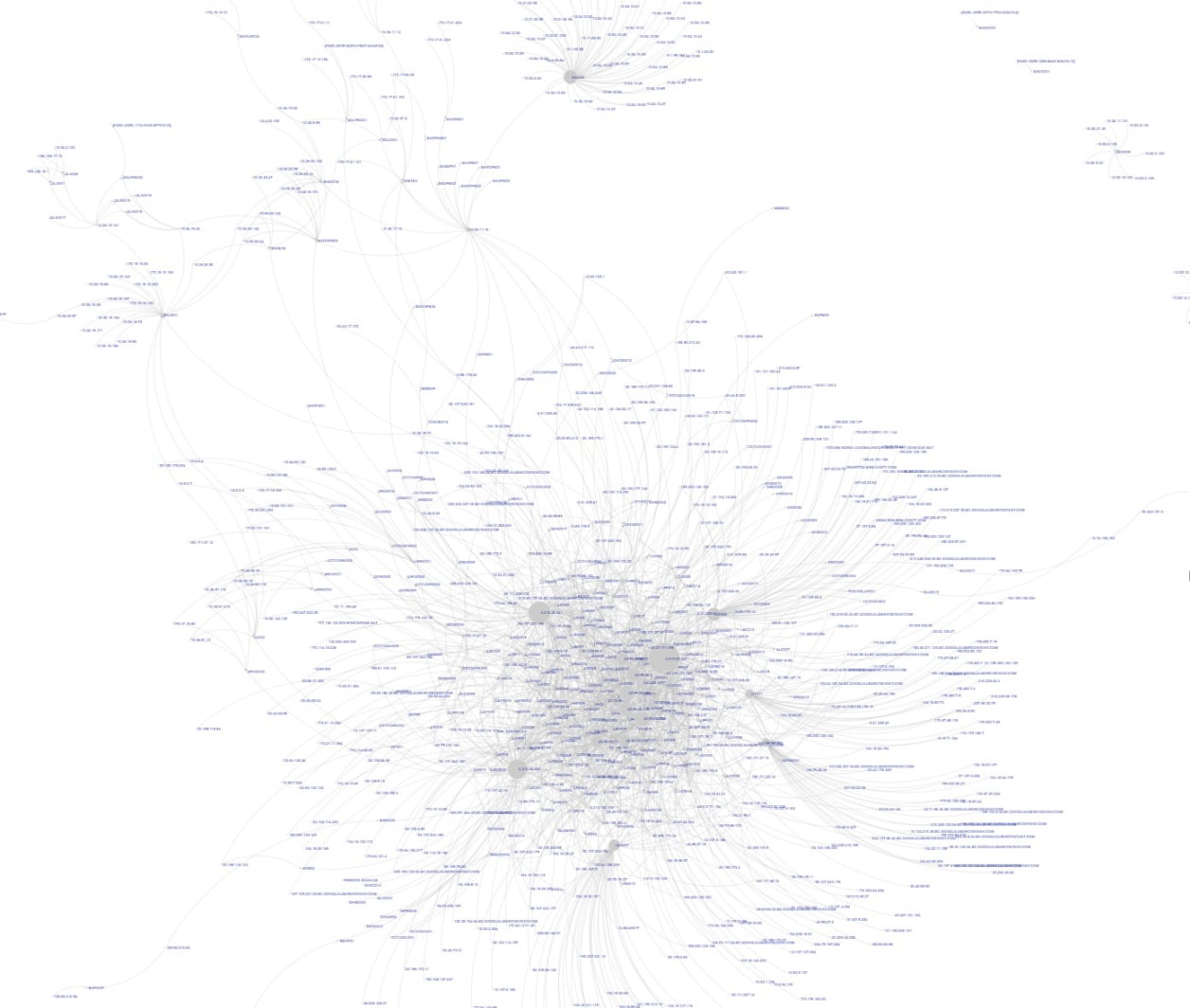
Hardware Asset Management
Discover, inventory, classify & assign ownership of IT & ICS hardware assets & their components across the lifecycle.
Software Asset Management
Track, catalog, ensure license compliance & allocate ownership to software assets throughout their lifecycle.
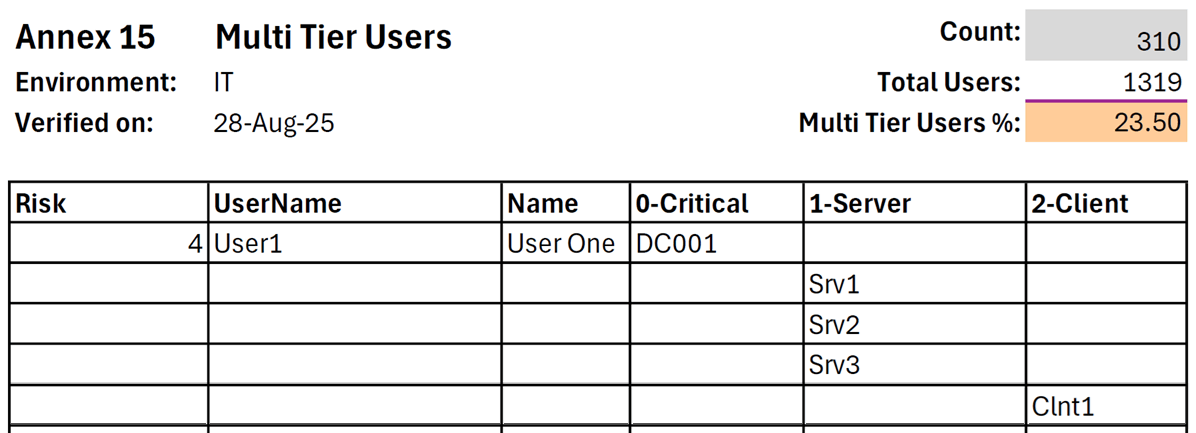
Identity Asset Management
Report domain and local user profiles, groups, privileges, access rights and permissions over their lifecycle.
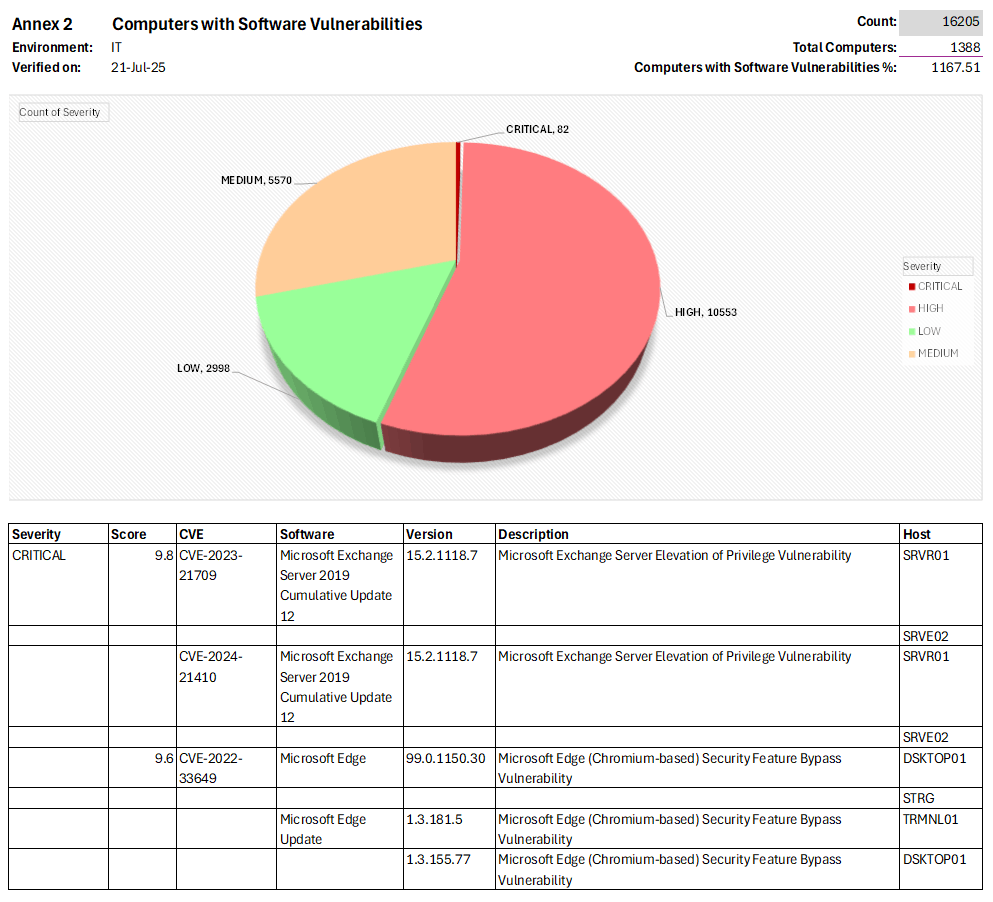
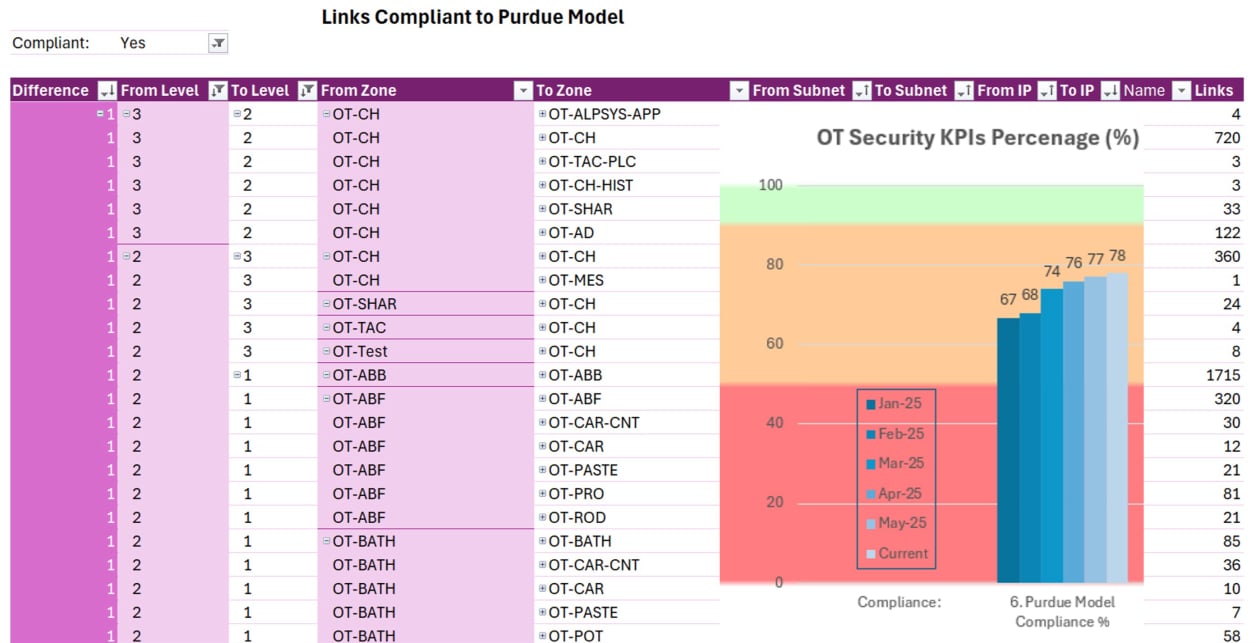
Vulnerability Management
Identify, assess, prioritize, report, validate & recommend mitigations for vulnerabilities in all assets.
Capacity Management
A critical aspect of security is Availability, which can't be achieved without monitoring Capacity to ensure better Uptime.











Contact us:
Email:
ping(a)secitics.com
LinkedIn:
SECITICS
WhatsApp:
+44 7707 381 530